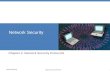
Endpoint Proliferation BILLION THINGS 50 B Y 2 0 2 0 T H E I N T E R N E T I S E X P E C T E D T O H A V E A N E S T I M A T E D QUADRILLION 13+ B Y 2 0 2 0 N U M B E R O F C O N N E C T I O N S W I L L E Q U A L Cybercriminals are taking advantage of the rapidly expanding attack surface found in today’s “any-to-any” world, where individuals are using any device to access business applications in a network environment that utilises decentralised services. X2 X3 X4 Millenials and the Workspace State of the Exploit of workers surveyed say they don’t mind if employers track their online behaviour. WORK ONLY respondents say they are supposed to use company-issued devices for work activity only. say they are allowed to use company devices for non work activity. of IT professionals say they have policies that prohibit devices being used for personal online activity. Security threats in today’s “any-to-any” world www.cisco.com/go/uk/networksecurity Global data center traffic is expected to quadruple over the next five years, and the fastest-growing component is cloud data. By 2016, global cloud traffic will make up nearly two-thirds of total data center traffic. Download the Cisco 2013 Annual Security Report to read the full insights and analysis. www.cisco.com/go/uk/networksecurity #networksecurity of organisations globally are already collecting, storing and analysing it say it will be a strategic priority in the year ahead believe it complicates security requirements quote lack of expertise and personnel as an inhibitor to effectively use it larger organisations are lower risk higher risk 250 employees Big Data of IT professionals acknowledge that employees break policy and use devices for personal activities in addition to doing work. The Nexus of Devices, Clouds and Applications Web malware encounters DOWNLOADER ANDROID INFOSTEALING EXPLICIT MALSCRIPT / IFRAME EXPLOIT Online ads are times more likely to deliver malicious content than pornography sites 182 #networksecurity 5000-10,000 employees 25,000+ employees more likely to encounter web malware Piecemeal security solutions, such as applying firewalls to a changeable network edge, doesn’t secure data that is now constantly in motion among devices, networks, and clouds. The Internet of Everything is quickly taking shape, so the security professional needs to think about how to shift their focus from simply securing endpoints and the network perimeter. There appears to be a disconnect between what employees think they can do with their company-issued devices and what policies IT actually dictate about personal usage. Lack of budget, time, appropriate solutions, IT staff and IT expertise are inhibitors to enterprise's ability to use big data effectively. Organisations should focus on security as part of the product design and development process, with timely vulnerability disclosures, and prompt/regular patch cycles. 2016

Network Security
Dec 17, 2014
Cybercriminals are taking advantage of the rapidly expanding attack surface found in today’s “any-to-any” world, where individuals are using any device to access business applications in a network environment that utilises decentralised services.
Welcome message from author
This document is posted to help you gain knowledge. Please leave a comment to let me know what you think about it! Share it to your friends and learn new things together.
Transcript

Endpoint Proliferation
BILLION THINGS50
BY 20
20 T
HE
INTE
RN
ET IS EXPECTED TO HAVE A
N ESTIM
ATED
QUADRILLION13+
BY 2
020
NUM
BER OF CONNECTIONS W
ILL EQU
AL
Cybercriminals are taking advantage of the rapidly expanding attack surface found in today’s “any-to-any” world, where individuals are using any device to access business applications in a network environment that utilises decentralised services.
X2 X3 X4
Millenials and the Workspace
State of the Exploit
of workers surveyedsay they don’t mindif employers track
their online behaviour.
WORK ONLY
respondents say they are supposed to use
company-issued devices for work
activity only.
say they are allowed to use company devices for non
work activity.
of IT professionals say they have policies that prohibit devices
being used for personal online activity.
Security threats in today’s “any-to-any” world
www.cisco.com/go/uk/networksecurity
Global data center tra�c is expected to quadruple over the next �ve years, and the fastest-growing component is cloud data.
By 2016, global cloud tra�c will make up nearly two-thirds of total data center tra�c.
Download the Cisco 2013 Annual Security Report to read the full insights and analysis.www.cisco.com/go/uk/networksecurity #networksecurity
of organisations globally are already collecting, storing and analysing it
say it will be a strategic priority in the year
ahead
believe it complicates security requirements
quote lack of expertise and personnel as an inhibitor to e�ectively
use it
larger organisations are
lower risk
higher risk
250employees
Big Data
of IT professionals acknowledge that
employees break policy and use devices for personal activities in
addition to doing work.
The Nexus of Devices, Clouds and Applications
Web malwareencounters
DOWNLOADER
ANDROID
INFOSTEALINGEXPLICITMALSCRIPT / IFRAME EXPLOIT
Online ads are times more likely to deliver malicious content than pornography sites
182
#networksecurity
5000-10,000employees
25,000+employees
more likely to encounterweb malware
Piecemeal security solutions, such as applying �rewalls to a changeable network edge, doesn’t secure data that is now constantly in motion among devices, networks, and clouds.
The Internet of Everything is quickly taking shape, so the security professional needs to think about how to shift their focus from simply securing endpoints and the network perimeter.
There appears to be a disconnect between what employees think they can do with their company-issued devices and what policies IT actually dictate about personal usage.
Lack of budget, time, appropriate solutions, IT sta� and IT expertise are inhibitors to enterprise's ability to use big data e�ectively.
Organisations should focus on security as part of the product design and development process, with timely vulnerability disclosures, and prompt/regular patch cycles.
2016
Related Documents