1 Implementing Security Compliance using Policy Groups Rob Zoeteweij Copyright – 2009 Zoeteweij Consulting

Welcome message from author
This document is posted to help you gain knowledge. Please leave a comment to let me know what you think about it! Share it to your friends and learn new things together.
Transcript

1
Implementing
Security Compliance
using Policy Groups
Rob Zoeteweij
Copyright – 2009 Zoeteweij Consulting

This Presentation…
• Is pretty technical
• Includes several (many) Screen dumps
• Covers OEM 10.2.0.4 – 10.2.0.5
• Gives you an insight overview of: How to … / How it
works
• Is about how we do this at Rabobank
2

3
Agenda
• Security at Rabobank
• Policy Rules
• Policy Groups
• Q & A

4
Security at Rabobank
• SOX
• Sarbanes-Oxley Act of 2002 (Wikipedia)
• Public Company Accounting Reform and Investor Protection
Act of 2002
• AKA – Sarbanes-Oxley, Sarbox or SOX
• Sponsors: Senator Paul Sarbanes and Representative
Michael G. Oxley
• In response to a number of major corporate and accounting
scandals incl Enron, Tyco International, Adelphia, Peregrine
Systems and WorldCom

5
Security at Rabobank
• SOX
• Not a static List
• Not a standard List
• Actual measurements can be different per Company
• Both organisational and technical

6
Security at Rabobank• SOX
• Measurements to keep compliant with RABO Security Rules
• Separation of facilities for Development, Testing and Production
• Developers / testers don’t have access to Production servers
• …
• Backups need to be available and tested
• Will be located on other location then source
• Need to be accessible for authorized employees only
• Audit logs need to be created
• All user actions must be logged and fully traceable to an individual
• …
• System access
• Based on “Least privilege” and “Need to know”
• ...

7
Security at Rabobank
• BIV code• Availability – Integrity – Confidentiality
• B - [1-3], I – [1-3], V – [1-3]
• Impact
• 1 – Low, 2 – Middle, 3 - High
• Example
• I = 2
• Financial Transactions that can be reversed without any (Image) damage
• I = 3
• Financial Transactions that can not be reversed without any (Image) damage

8
Security at Rabobank
• BIV code
• Availability – Integrity – Confidentiality
• Applied to Systems
• Applications
• Application Servers
• Servers (Hosts)
• Database Listeners
• Databases

9
Security at Rabobank
• BIV – codes in use
• 222 – 232 – 233 – 322 – 332 – 333

10
Security implementation in OEM
Policy Rules
• Policies
• Policies define the desired behaviour or characteristics of
systems
• A Policy is compliant if is determined that a target meets the
desired state
• Example: Oracle Home Executable Files Permission
• Ensure that all files in the ORACLE_HOME
directories (except for ORACLE_HOME/bin) do not
have public read, write and execute permissions
• If a Target does not meet this state, the Policy is violated

11
Security implementation in OEM
Policy Rules
• Policies – other examples
• Ensure database auditing is enabled
• Each activity in the database should be traceable
• Default passwords
• Ensure there are no default passwords for known accounts
• Open Ports
• Ensure that no unintended ports are left open
• …

12

13
Security implementation in OEM
Policy Rules
• Based on BIV codes in use
• Monitoring Templates
• Only Policy Rules included
• STP – <Target Type> - BIV<code>
• STP – Listener – BIV332
• STP – HTTP Server – BIV223
• STP – Cluster Database – BIV 322
• …

14

15
Security implementation in OEM
Policy Rules
• Use Groups to apply the Templates to the Targets
• Group organisation
• PG-<Target Type>_BIV<Code>_<Phase (Dev, Tst, Stg, Prd)>
• PG-Cluster_Databases_BIV233_Test
• PG-Database_Instances_BIV333_Prod
• …

16
Group PG-Cluster_Databases_BIV332_Test
Includes all Cluster Databases for which BIV code 332 apply

17

18

19

20

21

Security implementation in OEM
Policy Groups
• Policy Groups
• Compliance
• Logical Group of Policies
• 10.2.0.4 – 3 Out of Box Groups
• Secure Configuration for Oracle Database
• Secure Configuration for Oracle Listener
• Secure Configuration for Oracle Real Application Cluster
• 10.2.0.5 – Create your own
22

Security implementation in OEM
Policy Groups
23
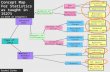
Policy Group
Rule 1
Rule 2
Rule n
Group
Target 1
Target 2
Target n
Evaluation
Schedule

24

25

26

27

28

29

30

31

Q & A
32
Related Documents