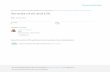
Myagmar, Gupta UIUC 2001 1 3G Security Principles • Build on GSM security • Correct problems with GSM security • Add new security features Source: 3GPP

Welcome message from author
This document is posted to help you gain knowledge. Please leave a comment to let me know what you think about it! Share it to your friends and learn new things together.
Transcript

Myagmar, Gupta UIUC 2001
1
3G Security Principles
• Build on GSM security
• Correct problems with GSM security
• Add new security features
Source: 3GPP

Myagmar, Gupta UIUC 2001
2
GSM Network Architecture
BSC
MS
PSTN/ISDN
BTS
EIREIRAUCAUC
HLRHLRVLRVLR
MSC
OMC
Um
A-bis
Circuit-switched technology
Voice Traffic
Mobilitymgt
A

Myagmar, Gupta UIUC 2001
3
GSM Security Elements, 1Key functions: privacy, integrity and confidentiality
• Authentication Protect from unauthorized service access
Based on the authentication algorithm A3(Ki, RAND)=> SRESProblems with inadequate algorithms
• Encryption Scramble bit streams to protect signaling and user dataCiphering algorithm A8(Ki, RAND) => Kc
A5(Kc, Data) => Encrypted DataNeed stronger encryption
• ConfidentialityPrevent intruder from identifying users by IMSITemporary MSINeed more secure mechanism

Myagmar, Gupta UIUC 2001
4
• SIM
A removable hardware security module
Manageable by network operators
Terminal independent
• Secure Application LayerSecure application layer channel between subscriber module and
home
network
• TransparencySecurity features operate without user assistance
Needs greater user visibility
• Minimized TrustRequires minimum trust between HE and SN
GSM Security Elements, 2

Myagmar, Gupta UIUC 2001
5
Problems with GSM Security, 1• Active Attacks
Impersonating network elements such as false BTS is possible
• Key TransmissionCipher keys and authentication values are transmitted in clear within
and between networks (IMSI, RAND, SRES, Kc)
• Limited Encryption ScopeEncryption terminated too soon at edge of network to BTS
Communications and signaling in the fixed network portion aren’t protected
Designed to be only as secure as the fixed networks
• Channel HijackProtection against radio channel hijack relies on encryption. However, encryption is not used in some networks.

Myagmar, Gupta UIUC 2001
6
Problems with GSM Security, 2
• Implicit Data IntegrityNo integrity algorithm provided
• Unilateral AuthenticationOnly user authentication to the network is provided.
No means to identify the network to the user.
• Weak Encryption AlgorithmsKey lengths are too short, while computation speed is increasing
Encryption algorithm COMP 128 has been broken
Replacement of encryption algorithms is quite difficult
• Unsecured TerminalIMEI is an unsecured identity
Integrity mechanisms for IMEI are introduced late

Myagmar, Gupta UIUC 2001
7
Problems with GSM Security, 3
• Lawful Interception & FraudConsidered as afterthoughts
• Lack of VisibilityNo indication to the user that encryption is on
No explicit confirmation to the HE that authentication parameters are properly used in SN when subscribers roam
• InflexibilityInadequate flexibility to upgrade and improve security functionality
over time

Myagmar, Gupta UIUC 2001
8
3G Network Architecture
Circuit/ SignalingGateway
2G/2.5G2G
IN Services
Call Agent
FeatureServer(s)
RNC
3G
Data + Packet Voice
Circuit Switch
CircuitNetwork
Packet Network(Internet)
Packet Gateway
Radio Access Control
Voice
Mobility Manager
IP CoreNetwork
IP RAN

Myagmar, Gupta UIUC 2001
9
New Security Features, 1
• Network AuthenticationThe user can identify the network
• Explicit IntegrityData integrity is assured explicitly by use of integrity algorithms
Also stronger confidentiality algorithms with longer keys
• Network SecurityMechanisms to support security within and between networks
• Switch Based SecuritySecurity is based within the switch rather than the base station
• IMEI IntegrityIntegrity mechanisms for IMEI provided from the start

Myagmar, Gupta UIUC 2001
10
New Security Features, 2• Secure Services
Protect against misuse of services provided by SN and HE
• Secure ApplicationsProvide security for applications resident on USIM
• Fraud DetectionMechanisms to combating fraud in roaming situations
• FlexibilitySecurity features can be extended and enhanced as required by new threats and services
• Visibility and ConfigurabilityUsers are notified whether security is on and what level of security
is available
Users can configure security features for individual services

Myagmar, Gupta UIUC 2001
11
New Security Features, 3• Compatibility
Standardized security features to ensure world-wide interoperability and roaming
At least one encryption algorithm exported on world-wide basis
• Lawful Interception
Mechanisms to provide authorized agencies with certain information about subscribers

Myagmar, Gupta UIUC 2001
12
Summary of 3G Security Features, 1
• User ConfidentialityPermanent user identity IMSI, user location, and user services
cannot be determined by eavesdropping
Achieved by use of temporary identity (TMSI) which is assigned by VLR
IMSI is sent in cleartext when establishing TMSI
USIM VLR
IMSI
TMSI allocation
TMSI acknowledgement
IMSI request

Myagmar, Gupta UIUC 2001
13
Summary of 3G Security Features, 2
• Mutual AuthenticationDuring Authentication and Key Agreement (AKA) the user and
network authenticate each other, and also they agree on cipher and integrity key (CK, IK). CK and IK are used until their time expires.
Assumption: trusted HE and SN, and trusted links between them.
After AKA, security mode must be negotiated to agree on encryption and integrity algorithm.
AKA process: USIM VLR HLR
AV request, send IMSI
Generate authentication data V(1..n) RAND(i) || AUTN(i)
Generate RES(i) Compare RES(i) and XRES(i)

Myagmar, Gupta UIUC 2001
14
Summary of 3G Security Features, 3
Generation of authentication data at HLR:
K
SQN RAND
f1 f2 f3 f4 f5
MAC XRES CK IK AK
AUTN := SQN AK || AMF || MAC
AV := RAND || XRES || CK || IK || AUTN
Generate SQN
Generate RAND
AMF

Myagmar, Gupta UIUC 2001
15
Summary of 3G Security Features, 4
Generation of authentication data in USIM:
K
SQN
RAND
f1 f2 f3 f4
f5
XMAC RES CK IK
AK
SQN AK AMF MAC
AUTN
Verify MAC = XMAC
Verify that SQN is in the correct range

Myagmar, Gupta UIUC 2001
16
Summary of 3G Security Features, 5
• Data IntegrityIntegrity of data and authentication of origin of signalling data must
be provided
The user and network agree on integrity key and algorithm during AKA and security mode set-up
f 9
COUNT-I DIRECTION
MESSAGE FRESH
IK
MAC -I
f 9
COUNT-I DIRECTION
MESSAGE FRESH
IK
XMAC -I
SenderUE or RNC
ReceiverRNC or UE

Myagmar, Gupta UIUC 2001
17
Summary of 3G Security Features, 6
• Data ConfidentialitySignalling and user data should be protected from eavesdropping
The user and network agree on cipher key and algorithm during AKA and security mode set-up
PLAINTEXTBLOCK
f8
COUNT-C DIRECTION
BEARER LENGTH
CK
KEYSTREAMBLOCK
CIPHERTEXTBLOCK
f8
COUNT-C DIRECTION
BEARER LENGTH
CK
KEYSTREAMBLOCK
PLAINTEXTBLOCK
SenderUE or RNC
ReceiverRNC or UE

Myagmar, Gupta UIUC 2001
18
Summary of 3G Security Features, 7
• IMEIIMEI is sent to the network only after the authentication of SNThe transmission of IMEI is not protected
• User-USIM AuthenticationAccess to USIM is restricted to authorized usersUser and USIM share a secret key, PIN
• USIM-Terminal AuthenticationUser equipment must authenticate USIM
• Secure ApplicationsApplications resident on USIM should receive secure messages over
the network
• VisibilityIndication that encryption is onIndication what level of security (2G, 3G) is available

Myagmar, Gupta UIUC 2001
19
Summary of 3G Security Features, 8
• ConfigurabilityUser configures which security features activated with particular servicesEnabling/disabling user-USIM authenticationAccepting/rejecting incoming non-ciphered callsSetting up/not setting up non-ciphered callsAccepting/rejecting use of certain ciphering algorithms
• GSM CompatibilityGSM user parameters are derived from UMTS parameters using the following conversion functions:
cipher key Kc = c3(CK, IK)random challenge RAND = c1(RAND)signed response SRES = c2(RES)
GSM subscribers roaming in 3GPP network are supported by GSM security context (example, vulnerable to false BTS)

Myagmar, Gupta UIUC 2001
20
Problems with 3G Security
• IMSI is sent in cleartext when allocating TMSI to the user
• The transmission of IMEI is not protected; IMEI is not a security feature
• A user can be enticed to camp on a false BS. Once the user camps on the radio channels of a false BS, the user is out of reach of the paging signals of SN
• Hijacking outgoing/incoming calls in networks with disabled encryption is possible. The intruder poses as a man-in-the-middle and drops the user once the call is set-up

Myagmar, Gupta UIUC 2001
21
References• 3G TS 33.120 Security Principles and Objectives
http://www.3gpp.org/ftp/tsg_sa/WG3_Security/_Specs/33120-300.pdf
• 3G TS 33.120 Security Threats and Requirementshttp://www.arib.or.jp/IMT-2000/ARIB-spec/ARIB/21133-310.PDF
• Michael Walker “On the Security of 3GPP Networks”http://www.esat.kuleuven.ac.be/cosic/eurocrypt2000/mike_walker.pdf
• Redl, Weber, Oliphant “An Introduction to GSM”Artech House, 1995
• Joachim Tisal “GSM Cellular Radio Telephony”John Wiley & Sons, 1997
• Lauri Pesonen “GSM Interception”http://www.dia.unisa.it/ads.dir/corso-security/www/CORSO-9900/a5/Netsec/netsec.html
• 3G TR 33.900 A Guide to 3rd Generation Securityftp://ftp.3gpp.org/TSG_SA/WG3_Security/_Specs/33900-120.pdf
• 3G TS 33.102 Security Architectureftp://ftp.3gpp.org/Specs/2000-12/R1999/33_series/33102-370.zip
• 3G TR 21.905 Vocabulary for 3GPP Specificationshttp://www.quintillion.co.jp/3GPP/Specs/21905-010.pdf
Related Documents